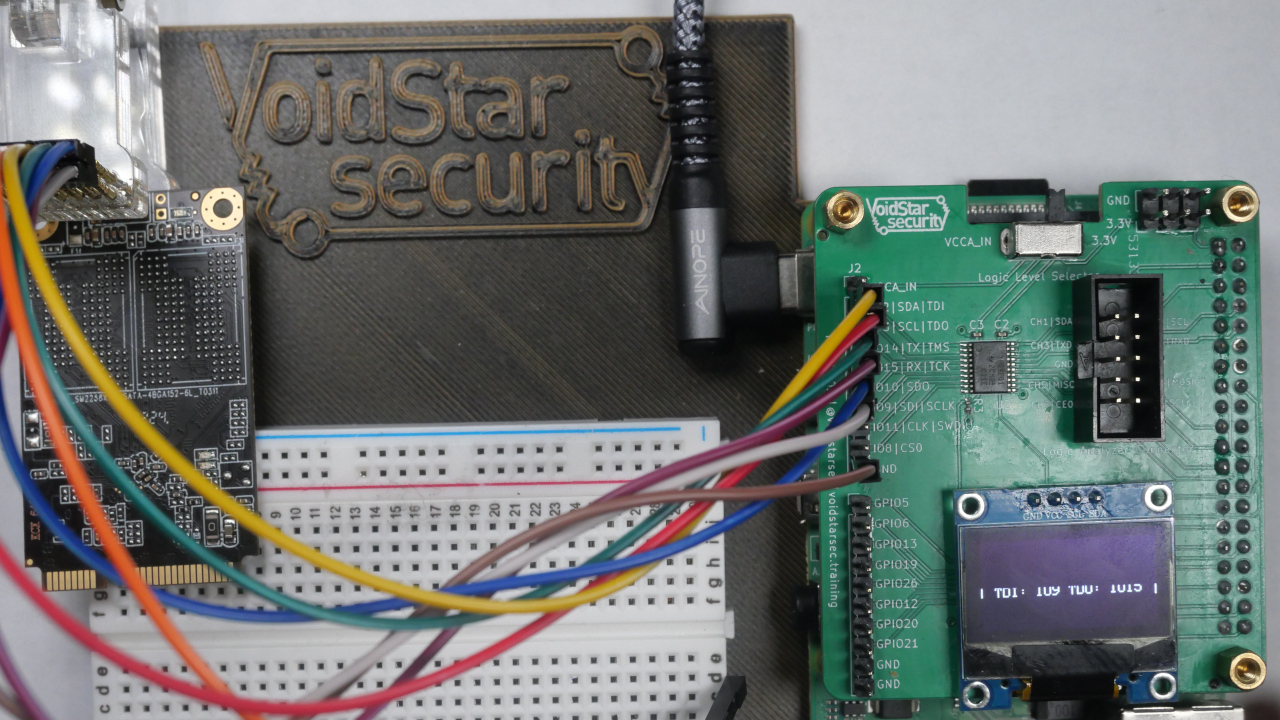
[Matthew “wrongbaud” Alt] is well-known round these elements for his {hardware} hacking and reverse-engineering classes, and today he’s bringing us a JTAG hacking primer that demoes some cool new {hardware} — the PiFEX (Pi Interface Explorer). Ever puzzled about these testpoint arrays on mSATA and M.2 SSDs? This write-up lays naked the secrets and techniques of such an SSD, utilizing a Pi 4, PiFEX, OpenOCD and a very good few open-source instruments for JTAG probing which you can simply use your self.
The PiFEX hat provides you level-shifted bidirectional GPIO connectors for UART, SPI, I2C, JTAG, SWD and doubtlessly far more, an OLED display screen to indicate any debugging info you would possibly want, and even a logic analyzer header so that you could check out your reverse-engineering progress.
 The instructed software program workflow pulls no punches both, proposing ease-of-use options like USB-Ethernet gadget mode and Jupyter notebooks. [wrongbaud] reveals us easy methods to discover JTAG among the many dozen testpads left on the SSD, get the SSD single-stepping by code, and dump a few of its reminiscence area as a take a look at. Filled with tips of the commerce like reverse-engineering gadgets on a sheet of paper you’ll be able to go away markings on, this write-up provides you a stable background in JTAG hacking, even should you solely have a Pi and an outdated SSD.
The instructed software program workflow pulls no punches both, proposing ease-of-use options like USB-Ethernet gadget mode and Jupyter notebooks. [wrongbaud] reveals us easy methods to discover JTAG among the many dozen testpads left on the SSD, get the SSD single-stepping by code, and dump a few of its reminiscence area as a take a look at. Filled with tips of the commerce like reverse-engineering gadgets on a sheet of paper you’ll be able to go away markings on, this write-up provides you a stable background in JTAG hacking, even should you solely have a Pi and an outdated SSD.
So how are you going to get your fingers on one? [wrongbaud] says the plan is to open supply each the PiFEX {hardware} and software program within the close to future. Till till then, it appears to be like like not less than the {hardware} it wouldn’t be too laborious to re-implement it your self should you needed to get the hold of reverse engineering with the Raspberry Pi.
[Matthew “wrongbaud” Alt] is an effective pal of Hackaday neighborhood. He’s stopped by to host a reverse engineering Hack Chat, and ran a HackadayU class on Ghidra. His reverse-engineering journeys are at all times an informative learn, from utilizing arcade machines as a Linux hacking primer, to hacking a cryptocurrency wallet by glitching assaults.