Government Abstract
The “Safety Alert” rip-off is a prevalent tech-support fraud that threatens each Home windows and Apple customers. It exploits the belief of customers by masquerading as an official help web site, utilizing faux pop-up warnings to lure customers into dialing rip-off cellphone numbers by conveying a way of urgency. The final word purpose is gaining distant entry to the consumer’s system and pilfering private information to extort cash.
Combating a “Safety Alert” rip-off is troublesome on many fronts as a result of more often than not attackers leverage newly registered domains, which suggests there’s a lack of malicious OSINT (open-source intelligence), and they can bypass conventional detection strategies. To achieve distant entry, attackers want the top consumer to name right into a fraudulent help crew to put in a Distant Desktop Protocol (RDP) device. An endpoint detection and response (EDR) device may not catch the preliminary intrusion as such instruments are additionally used for respectable enterprise causes. Essentially the most profitable strategy to fight phishing/scams is by end-user training and communication with the IT division.
In a latest incident, a faux “Microsoft Safety Alert” area focused one in all our Managed Endpoint Security with SentinelOne clients, inflicting alarm for the top customers and IT employees, however luckily, the top consumer didn’t fall into the lure of calling the fraudulent quantity.
The client instantly contacted their assigned Menace Hunter for help and steerage, and the Menace Hunter was in a position to rapidly make the most of the safety measures in place, find a number of domains, and report them to the Alien Labs menace intelligence crew.
AT&T Cybersecurity was one of many first cybersecurity corporations to alert on the domains and share the knowledge through the Open Threat Exchange (OTX) menace intelligence sharing group, serving to different organizations defend in opposition to it.
Investigation
Preliminary Alarm Overview
Indicators of Compromise (IOCs)
The preliminary safety layers failed to lift alarms for a number of causes. First, the firewalls didn’t block the area as a result of it was newly registered and due to this fact not but on any recognized block lists. Second, the platform didn’t create any alarms as a result of the area’s SSL certificates had been correctly configured. Lastly, the EDR device didn’t alert as a result of no downloads had been initiated from the web site. The primary indication of a problem got here from an finish consumer who feared a hack and reported it to the inner IT crew.
Using the knowledge offered by the top consumer, the Menace Hunter was in a position to find the consumer’s asset. Sniffing the URL information revealed a misleading “Microsoft Safety Alert” area and a counterfeit McAfee web site. These had been detected largely due to enhancements really helpful in the course of the buyer’s month-to-month conferences with the Menace Hunter, together with a advice to activate the SentinelOne Deep Visibility browser extension, which is the device that was instrumental in capturing URL info with better accuracy after all of the redirects.
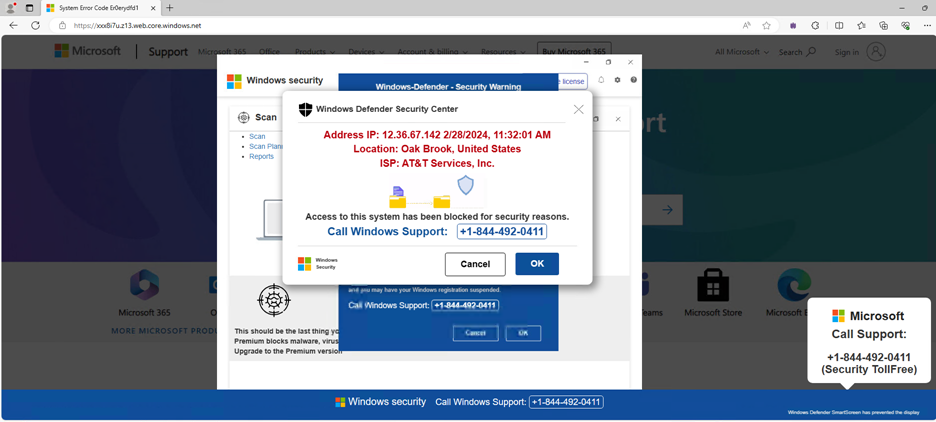
Determine I – Faux Microsoft Help web page
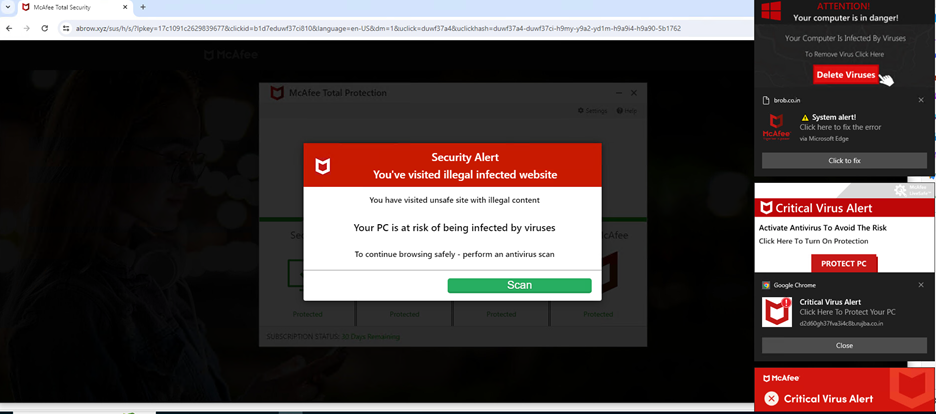
Determine 2 – Faux McAfee web page
Artifact (Indicator of Compromise) IOC Faux McAfee Web page bavareafastrak[.]org Web site Internet hosting Rip-off Pages Galaxytracke[.]com Zip file hash Tizer.zip – 43fb8fb69d5cbb8d8651af075059a8d96735a0d5
Determine 3 – Indicators of compromise
Expanded Investigation
Occasions Search
With the understanding that the endpoint will need to have accessed a web site that includes the fraudulent help web page, the seek for the occasion was streamlined to give attention to URL requests inside a selected time-frame. To filter out pointless noise, it was essential to quickly exclude genuine domains which might be related to generally used instruments inside the group. As soon as the menace hunter fine-tuned their search parameters, it took a eager eye and leveraging a sandbox surroundings to search out the area associated to the fraudulent help web page that the top consumer had encountered. This menace hunt uncovered a second area that was posing as a faux McAfee web page inside the similar time-frame.
Occasion Deep-Dive
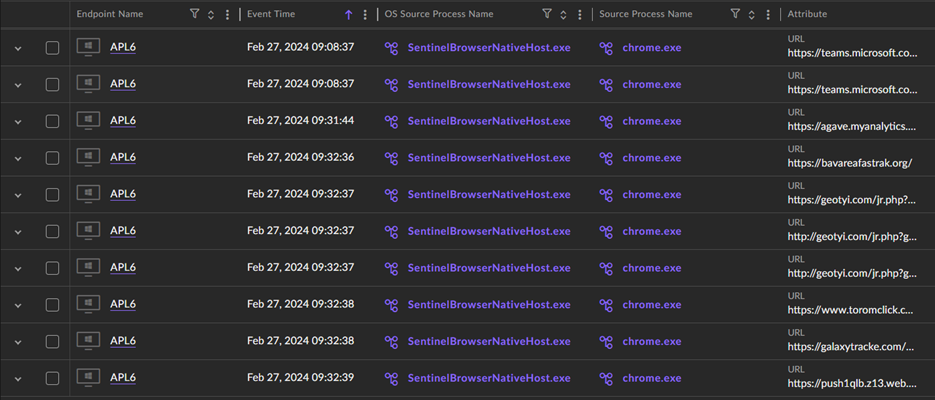
Whereas OSINT searches yielded restricted info, the Menace Hunter might manually discover the web site to achieve a greater understanding of its operations. Nonetheless, earlier than doing this, it was crucial to know how the consumer had arrived on the web site. Utilizing SentinelOne Storyline know-how, the Menace Hunter might correlate the sequence of occasions main as much as the web site go to. They deduced that the consumer doubtless visited the location via a hyperlink shared on the Microsoft Groups internet app, which redirected the consumer to the fraudulent help web page through a clickable advert.
Determine 4 – SentinelOne Deep Visibility findings
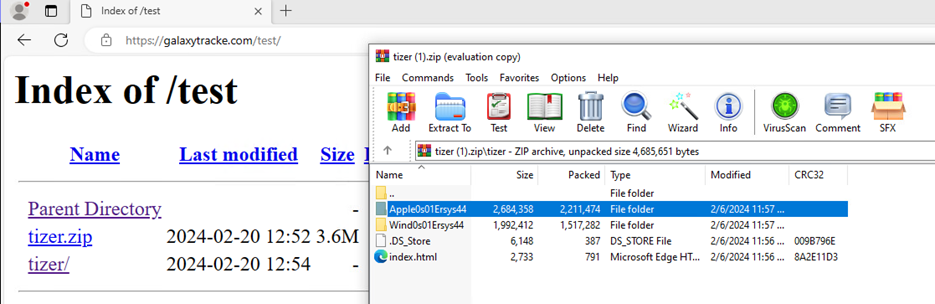
Luckily, SentinelOne was in a position to seize the primary area earlier than the consumer was redirected to the touchdown web page. Using digital machines as a security precaution, the Menace Hunter was in a position to go to the area the place they found it was internet hosting a number of directories, a few of which contained HTML code that was used to assemble the fraudulent help web page. Apparently, some directories contained .zip recordsdata that held HTML recordsdata for different forms of fraudulent help pages, equivalent to Apple, full with all the pictures and sounds essential to create the pages.
Determine 5 – Web site internet hosting faux “Safety Alert” websites
Reviewing for Further Indicators
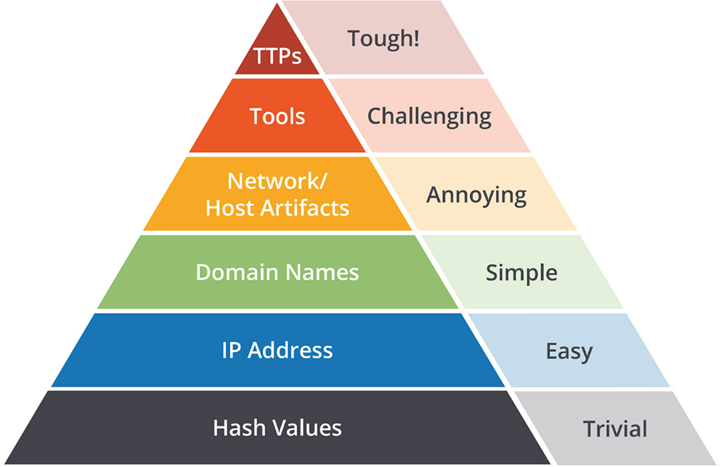
If we evaluation the Pyramid of Pain, which is a conceptual mannequin that categorizes IOCs and attacker ways, methods, and procedures (TTPs) in line with how troublesome they’re for attackers to alter, we see that domains are the third-lowest layer. However how does the attacker transfer up the Pyramid? By giving finish customers a fraudulent help web page to name! Domains will change each day, however one TTP that attackers will all the time want is having access to the machine. On this case, it was by having the Menace Hunter obtain the UltraViewer RDP device.
Determine 6 – Pyramid of Ache
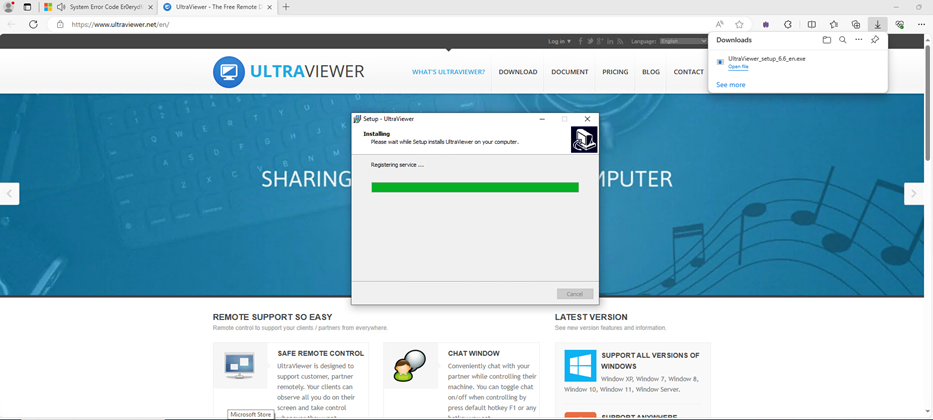
Because of SentinelOne’s app stock capabilities, by correlating a profitable URL occasion match with the set up of this device, we will gauge the extent to which the top consumer might have fallen prey to the rip-off. We additionally reviewed our fleet of managed clients and located no installations of the UltraViewer device that might point out a consumer had been efficiently compromised.
Determine 7 – Obtain of UltraViewer assisted by scammer
Combating Adversaries
Our Alien Labs menace intelligence crew promptly added the 2 domains we recognized to an OTX pulse, which permits us to alert on any property that go to these web sites. We advocate that our clients conduct ongoing coaching with finish customers to assist forestall them from falling sufferer to the newest scams. Moreover, the malicious domains detected ought to be blocked on the firewall. Though the menace actors behind these web sites have modified their show, the domains stay energetic. They’ll proceed to be monitored on OTX due to their previous exercise and potential future use.
Blocking IOCs is just one element of a cybersecurity technique. And for this reason, throughout month-to-month calls with our Managed Endpoint Safety with SentinelOne clients, we not solely talk about the outcomes of our newest menace hunts but additionally evaluation functions put in of their environments. We offer steerage on how you can improve visibility of their environments, and a method to do that is by activating the SentinelOne Deep Visibility extension, which might considerably enhance the monitoring of URL occasions, equivalent to those who occurred on this incident.
| Artifact | (Indicator of Compromise) IOC |
|---|---|
| Faux McAfee Web page | bavareafastrak[.]org |
|
Web site Internet hosting Rip-off Pages |
Galaxytracke[.]com |
| Zip file hash | Tizer.zip – 43fb8fb69d5cbb8d8651af075059a8d96735a0d5 |