
In Could 2023, in a menace hunt throughout Sophos Managed Detection and Response telemetry, Sophos MDR’s Mark Parsons uncovered a posh, long-running Chinese language state-sponsored cyberespionage operation we’ve got dubbed “Crimson Palace” focusing on a high-profile authorities group in Southeast Asia.
MDR launched the hunt after the invention of a DLL sideloading approach that exploited VMNat.exe, a VMware part. Within the investigation that adopted, we tracked no less than three clusters of intrusion exercise from March 2023 to December 2023. The hunt additionally uncovered beforehand unreported malware related to the menace clusters, in addition to a brand new, improved variant of the previously-reported EAGERBEE malware. In keeping with our customary inner nomenclature, Sophos tracks these clusters as Cluster Alpha (STAC1248), Cluster Bravo (STAC1807), and Cluster Charlie (STAC1305).
Whereas our visibility into the focused community was restricted because of the extent to which Sophos endpoint safety had been deployed throughout the group, our investigations additionally discovered proof of associated earlier intrusion exercise relationship again to early 2022. This led us to suspect the menace actors had long-standing entry to unmanaged belongings throughout the community.
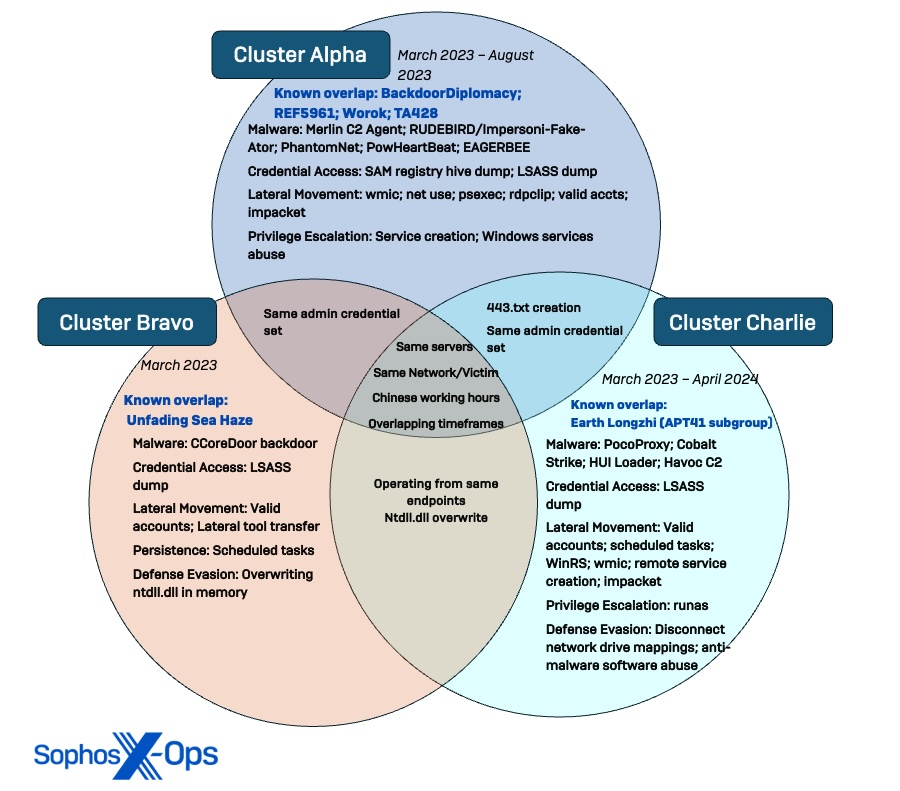
The clusters have been noticed utilizing instruments and infrastructure that overlap with different researchers’ public reporting on Chinese language menace actors BackdoorDiplomacy, REF5961, Worok, TA428, the recently-designated Unfading Sea Haze and the APT41 subgroup Earth Longzhi. Moreover, Sophos MDR has noticed the actors trying to gather paperwork with file names that point out they’re of intelligence worth, together with army paperwork associated to methods within the South China Sea.
Based mostly on our investigation, Sophos asserts with excessive confidence the general objective behind the marketing campaign was to take care of entry to the goal community for cyberespionage in help of Chinese language state pursuits. This contains accessing crucial IT methods, performing reconnaissance of particular customers, accumulating delicate army and technical info, and deploying varied malware implants for command-and management (C2) communications. We have now average confidence that these exercise clusters have been a part of a coordinated marketing campaign below the path of a single group. Sophos is sharing indicators and context for the Crimson Palace marketing campaign in hopes of contributing to additional public analysis and serving to different defenders and analysts disrupt associated exercise.
Sophos has repeatedly shared the small print of the intrusion with licensed contacts for the focused group. Sophos MDR continues to intently monitor this surroundings to report the scope and scale of the continuing exercise to the sufferer group, in addition to accumulate intelligence to trace assault techniques and generate up to date detections for all Sophos prospects. Sophos has additionally shared intelligence from this marketing campaign with authorities and trade companions, together with Elastic Security and Trend Micro who’ve beforehand reported on comparable threats.
Key findings of our investigation included:
- Novel malware variants: Sophos recognized the usage of beforehand unreported malware we name CCoreDoor (concurrently found by BitDefender) and PocoProxy, in addition to an up to date variant of EAGERBEE malware with new capabilities to blackhole communications to anti-virus (AV) vendor domains within the focused group’s community. Different noticed malware variants embody NUPAKAGE, Merlin C2 Agent, Cobalt Strike, PhantomNet backdoor, RUDEBIRD malware, and the PowHeartBeat backdoor.
- Intensive dynamic hyperlink library (DLL) sideloading abusing Home windows and anti-virus binaries: The Crimson Palace marketing campaign included over 15 distinct DLL sideloading situations, most of which abused Home windows Providers, reliable Microsoft binaries, and AV vendor software program.
- Excessive prioritization of evasive techniques and instruments: The menace actors leveraged many novel evasion methods, resembling overwriting ntdll.dll in reminiscence to unhook the Sophos AV agent course of from the kernel, abusing AV software program for sideloading, and utilizing varied methods to check essentially the most environment friendly and evasive strategies of executing their payloads.
- Three distinct clusters with overlaps indicating coordination: Whereas Sophos recognized three distinct patterns of conduct, the timing of operations and overlaps in compromised infrastructure and aims counsel no less than some stage of consciousness and/or coordination between the clusters within the surroundings.
Due to the quantity of intelligence uncovered in our investigation into this marketing campaign, we’ve got divided our report in two. This text gives an summary of the marketing campaign and highlights the overlap of the noticed exercise clusters and the malware distinctive to them. Full technical evaluation of the exercise clusters is supplied in a technical appendix, additionally printed at the moment. We have now supplied hyperlinks from inside this text to related parts of the detailed evaluation in that article.
Prior Compromise
The focused group is categorized by Sophos as a “blended property,” which means Sophos Managed Detection and Response (MDR) and Prolonged Detection and Response (XDR) protection are solely deployed to a subset of endpoints. Due to this, the Sophos staff lacks full visibility over all belongings within the surroundings, main us to evaluate the total extent of the compromise probably extends past Sophos-protected endpoints and servers.
Whereas preliminary entry occurred outdoors Sophos’ visibility into the group, we noticed associated exercise relationship again to early 2022. That included a March 2022 detection of NUPAKAGE malware (Troj/Steal-BLP), a personalized instrument used for exfiltration that has been publicly attributed by Trend Micro to the Chinese language menace group Earth Preta (aka Mustang Panda).
The group later enrolled a subset of their endpoints with Sophos’ MDR service. Detections of suspicious exercise prompted the MDR Operations staff to research the group’s property. This included a December 2022 investigation into intrusion exercise the place DLL-stitching was used to obfuscate and deploy two malicious backdoors on course area controllers. At the moment, the detections Troj/Backdr-NX and ATK/Stowaway-C have been deployed throughout Sophos prospects to detect the stitched DLL payloads, and a behavioral detection was created to detect when a service DLL is added to the Home windows registry.
A deeper evaluation of those earlier compromises might be discovered here.
Evaluation of Exercise Clusters
The menace hunt that recognized the exercise clusters lined on this report started in Could 2023. Throughout the investigation, Sophos analysts recognized a number of patterns indicating distinct clusters of conduct have been working within the community throughout the identical interval. These included:
- Authentication information, together with supply subnet, workstation hostname, and account utilization
- Methods, together with particular instructions and choices, repeatedly utilized by the attackers
- Attacker C2 infrastructure
- Distinctive instruments and the paths the place they have been deployed
- Focused person accounts and hosts
- Timing of the noticed exercise
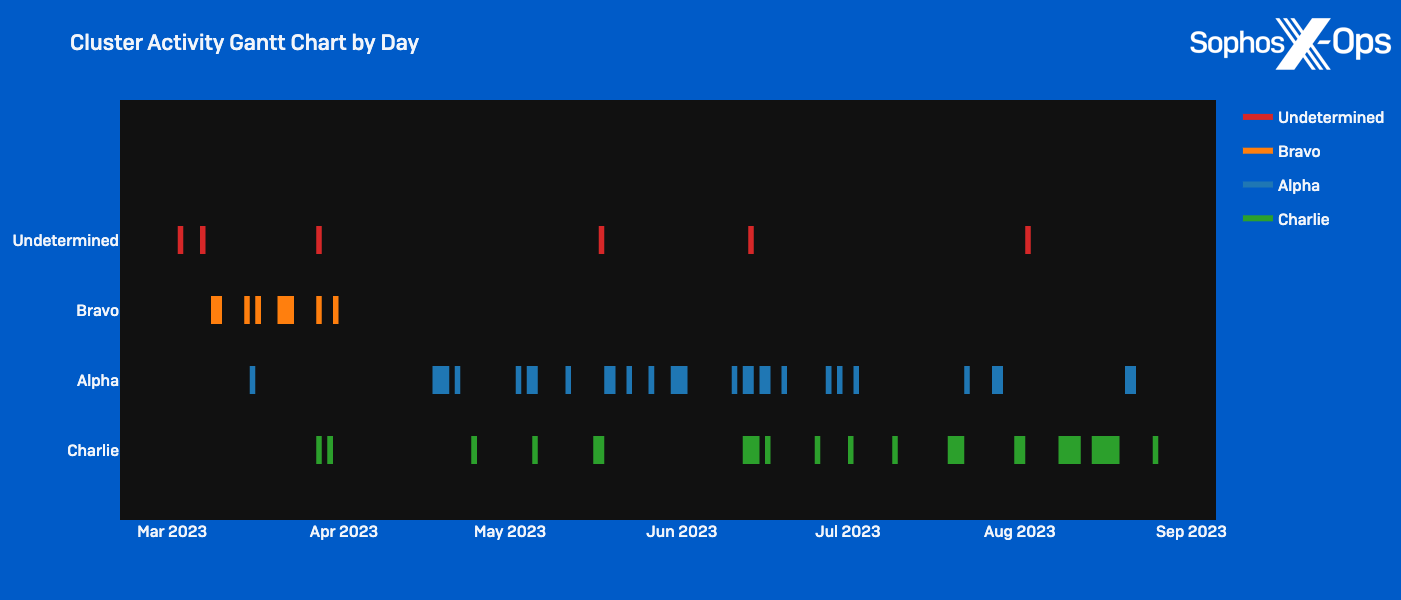
Based mostly on these patterns, we assess with average confidence that the espionage marketing campaign consisted of no less than three exercise clusters with separate units of infrastructure and TTPs coexisting within the goal group’s community from no less than March to September 2023.
For extra info on the assault chains of the noticed clusters and particulars on the novel techniques and tooling, consult with the attack chain details report.
Cluster Alpha (STAC1248)
We noticed Cluster Alpha exercise from early March to no less than August 2023. That exercise included a number of sideloading makes an attempt to deploy varied malware and set up persistent C2 channels inside shopper and server subnets. All through this exercise, we noticed mutations of profitable techniques that resulted in the identical consequence, indicating the menace actors might have been leveraging the sufferer community as a playground to check completely different methods. Along with utilizing distinctive methods to disable AV protections and escalate privileges, the actor working in Cluster Alpha prioritized comprehensively mapping server subnets, enumerating administrator accounts, and conducting reconnaissance on Energetic Listing infrastructure.
Key observations
- Deployment of latest EAGERBEE malware variants with up to date functionality of modifying packets to disrupt safety agent community communications
- Use of a number of persistent C2 channels together with Merlin Agent, PhantomNet backdoor, RUDEBIRD malware, EAGERBEE malware, and PowHeartBeat backdoor
- Leverage of unusual LOLBins instsrv.exe and srvany.exe for service persistence with elevated SYSTEM privileges
- Facet-loading of eight distinctive DLLs abusing Home windows Providers, reliable Microsoft binaries, and endpoint safety distributors’ software program
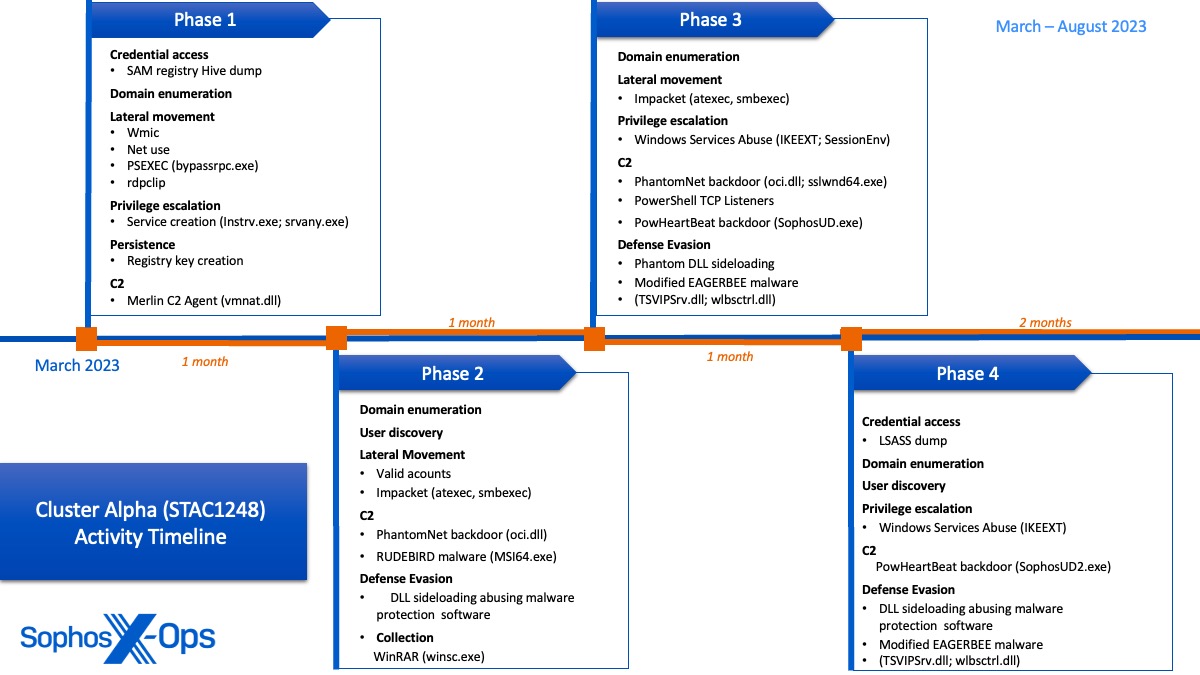
An additional evaluation of Cluster Alpha might be discovered here.
Cluster Bravo (STAC1807)
Whereas the exercise within the different two clusters spanned over a number of months, exercise in Cluster Bravo was solely noticed within the focused group’s surroundings for a three-week span in March 2023 (coinciding with the primary session of China’s 14th Nationwide Folks’s Congress). Characterised as a mini cluster due to its quick period, Cluster Bravo exercise was primarily targeted on utilizing legitimate accounts to unfold laterally all through the community, with the objective of sideloading a novel backdoor to determine C2 communications and keep persistence on course servers.
Key noticed conduct included:
- Deployment of a backdoor (which we dubbed CCoreDoor, and BitDefender has designated as EtherealGh0st) to maneuver laterally, set up exterior C2 communications, carry out discovery, and dump credentials (concurrently found by BitDefender)
- Use of renamed variations of a signed a signed side-loadable binary (mscorsvw.exe) to obfuscate backdoor deployment and transfer laterally from the beachhead host to different distant servers
- Connections made to different hosts that have been verified to be operating inside different in-country authorities organizations who might also be doubtlessly compromised
- Overwriting of ntdll.dll in reminiscence with an on-disk model to unhook the Sophos endpoint safety agent course of from the kernel
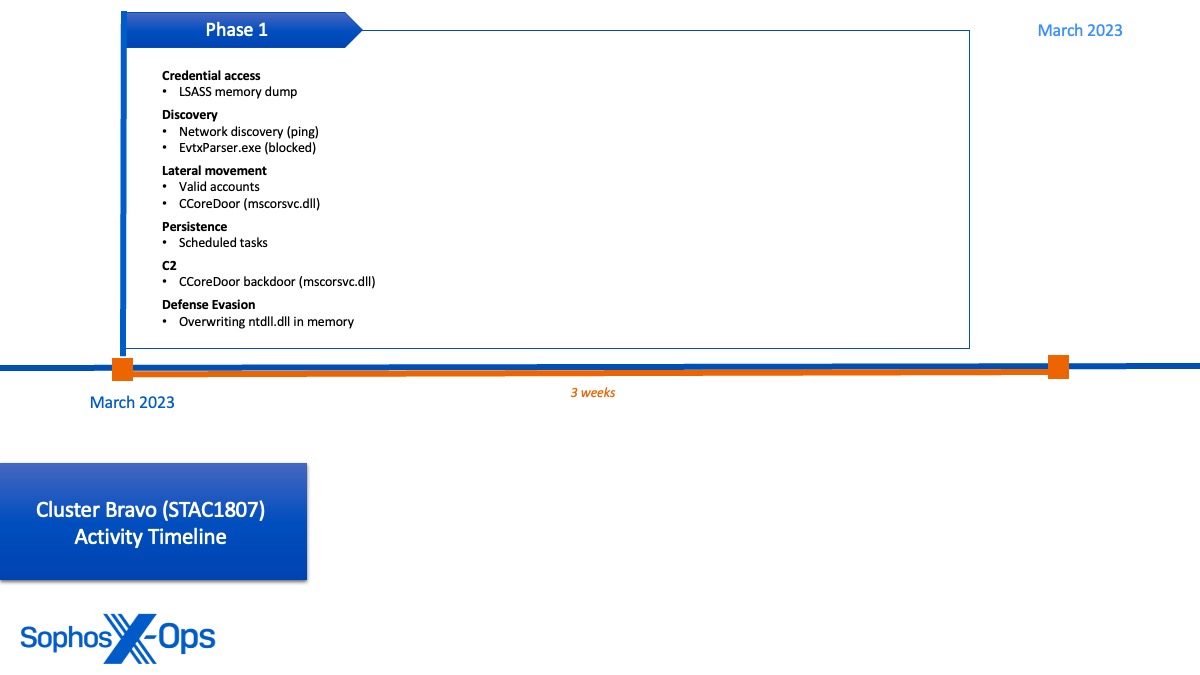
Additional particulars on Cluster Bravo might be discovered here.
Cluster Charlie (STAC1305)
Sophos MDR hunters noticed Cluster Charlie exercise within the goal community for the longest interval, with operations spanning from March to no less than April 2024. Showing to extremely prioritize entry administration, the actor deployed a number of implants of a beforehand unidentified malware, dubbed PocoProxy, to determine persistence on course methods and rotate to new exterior C2 infrastructure.
In a day in June 2023, exercise in Cluster Charlie spiked because the actors carried out a few of their noisiest discoveries, together with mass evaluation of Occasion Logs for environment-wide person and community reconnaissance. The output of this reconnaissance was used to conduct automated ping sweeps over the community, with the suspected objective of mapping all customers and endpoints within the community. Notably, this present day was a vacation within the goal group’s nation, suggesting the menace actor was saving their most overt exercise for a day with a decrease anticipated response time. Whereas discovery and lateral motion efforts continued over the subsequent a number of months, Cluster Charlie exercise was later noticed trying to exfiltrate delicate info, which primarily based on the file names concerned and information collected, we assess with excessive confidence was for espionage functions.
Key noticed conduct included:
- Deployment of a number of samples of a beforehand unreported malware (which we name PocoProxy) for persistent C2 communications
- Assortment and exfiltration of a giant quantity of knowledge, together with delicate army and political paperwork, information on infrastructure structure, and credentials/tokens for additional in-depth entry
- Deployment of a customized malware loader known as HUI loader to inject a Cobalt Strike Beacon into mstsc.exe, which was blocked by Sophos HMPA protections
- Injection of an LSASS logon credential interceptor into svchost.exe to seize credentials on area controllers
- Execution of wevtutil instructions to conduct particular person reconnaissance, utilizing the output to launch automated ping sweeps towards 1000’s of targets throughout the community
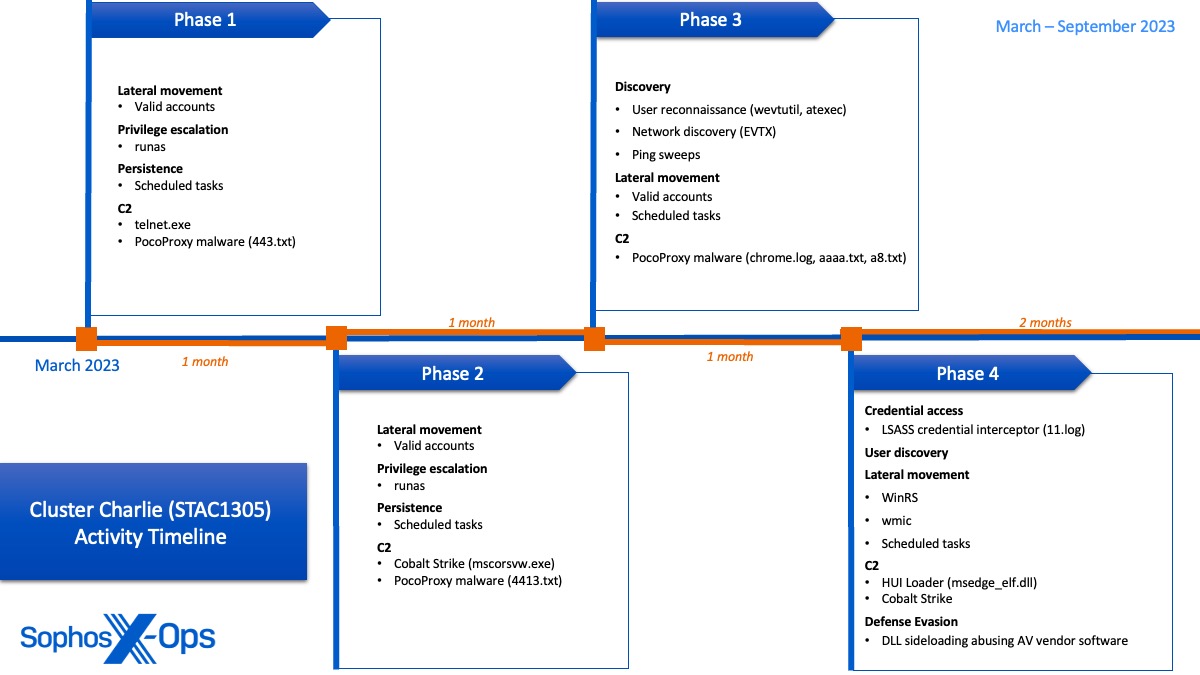
Additional particulars on Cluster Charlie might be discovered here.
Attribution and Cluster Overlap
Based mostly on mixed facets of victimology, temporal evaluation, infrastructure, tooling, and actions on aims, we assess with excessive confidence the noticed exercise clusters are related to Chinese language state-sponsored operations.
Along with the timing of exercise within the clusters aligning with customary Chinese language working hours, a number of noticed TTPs overlap with trade reporting on Chinese language-nexus actors. Moreover, the goal community is a high-profile authorities group in a Southeast Asian nation recognized to have repeated battle with China over territory within the South China Sea. We assess the objective behind this marketing campaign is long-term espionage, evidenced by the three clusters creating redundant C2 channels throughout the community to make sure persistent entry and accumulate info associated to Chinese language state pursuits.
Constant Chinese language Working Hours
In accordance with our evaluation of exercise frequency, exercise within the clusters primarily occurred between 00:00 and 09:00 Coordinated Common Time (UTC) Monday by Friday, equal to typical Chinese language working hours of 8am to 5pm China Customary Time (CST).
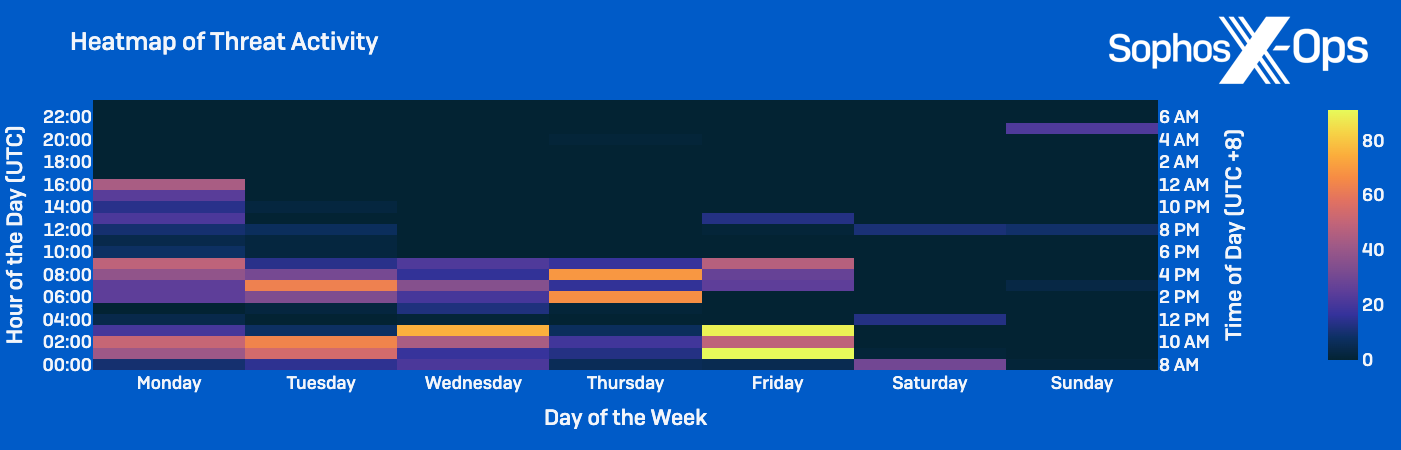
Analyzing the Clusters’ Working Schedules
Temporal evaluation of the person exercise clusters revealed distinct variations within the timing of their operations, the place they have been not often noticed performing in depth actions on the identical day.
In actual fact, the clusters seem to schedule exercise round each other, lending proof the menace actors within the clusters might concentrate on the others’ actions. At some factors, Cluster Alpha and Cluster Charlie exercise appeared to alternate by day, resembling when exercise in Cluster Alpha paused for 3 days as Cluster Charlie’s spike of exercise occurred in June.
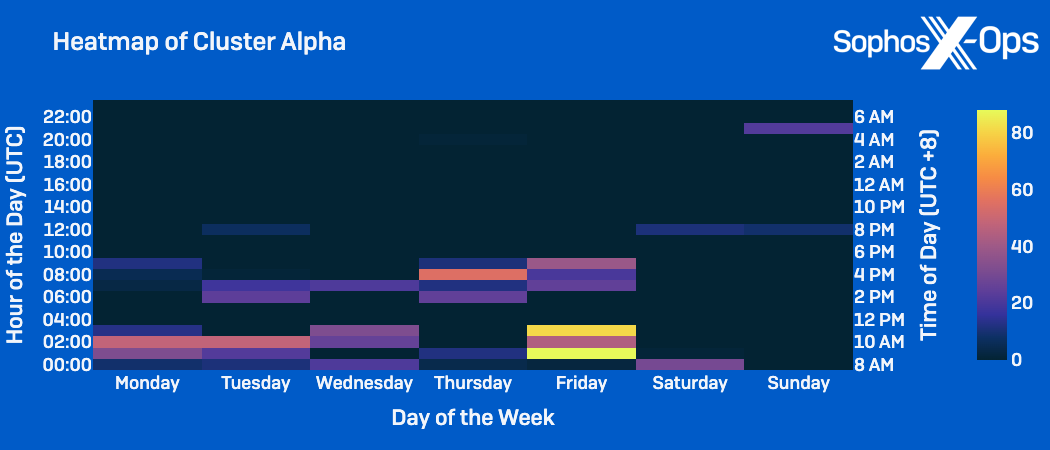
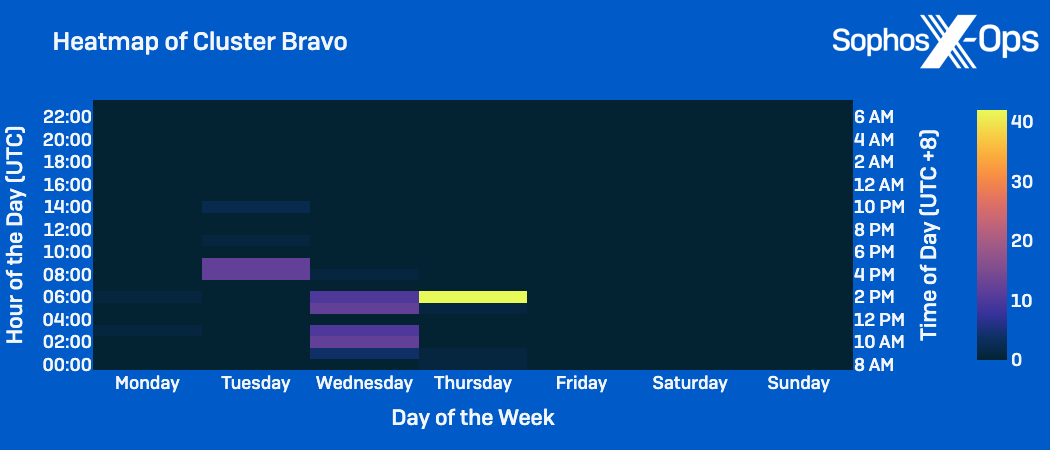
In analyzing the time and days of the week the clusters have been most energetic, we seen comparable distinctions:
- Cluster Alpha exercise: Typically occurred on weekdays throughout the conventional working hours of 8am to 5pm CST; Peaked on Friday.
- Cluster Bravo exercise: Occurred inside conventional working hours of 8am to 5pm CST, however was focused on Tuesday, Wednesday, and Thursday.
- Cluster Charlie exercise: Various essentially the most outdoors customary working hours; Exercise peaked Monday by Wednesday 12pm to 6pm CST.
- The focus of Cluster Charlie exercise on Monday from 3pm to 12am CST aligns with the cluster’s spike of exercise in June.
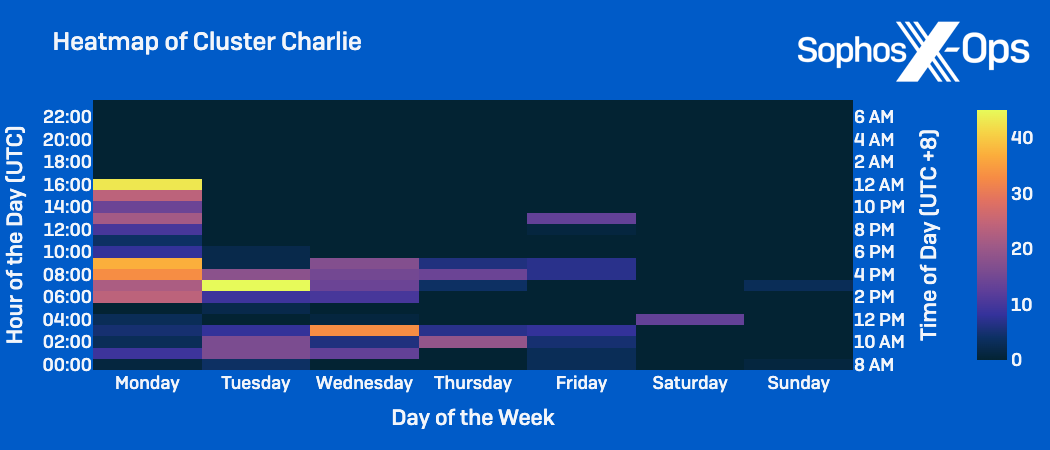
Attributing Clustered Exercise
Whereas Sophos MDR asserts with excessive confidence the noticed menace clusters are related to Chinese language state-sponsored exercise, we’re refraining from making attributions to recognized menace actor teams at the moment. One purpose is that Chinese language menace teams are generally recognized to share infrastructure and tooling, making attribution tougher. We have now, nonetheless, recognized areas of overlap between our particular observations and third-party reporting so as to add context to the exercise.
Cluster Alpha
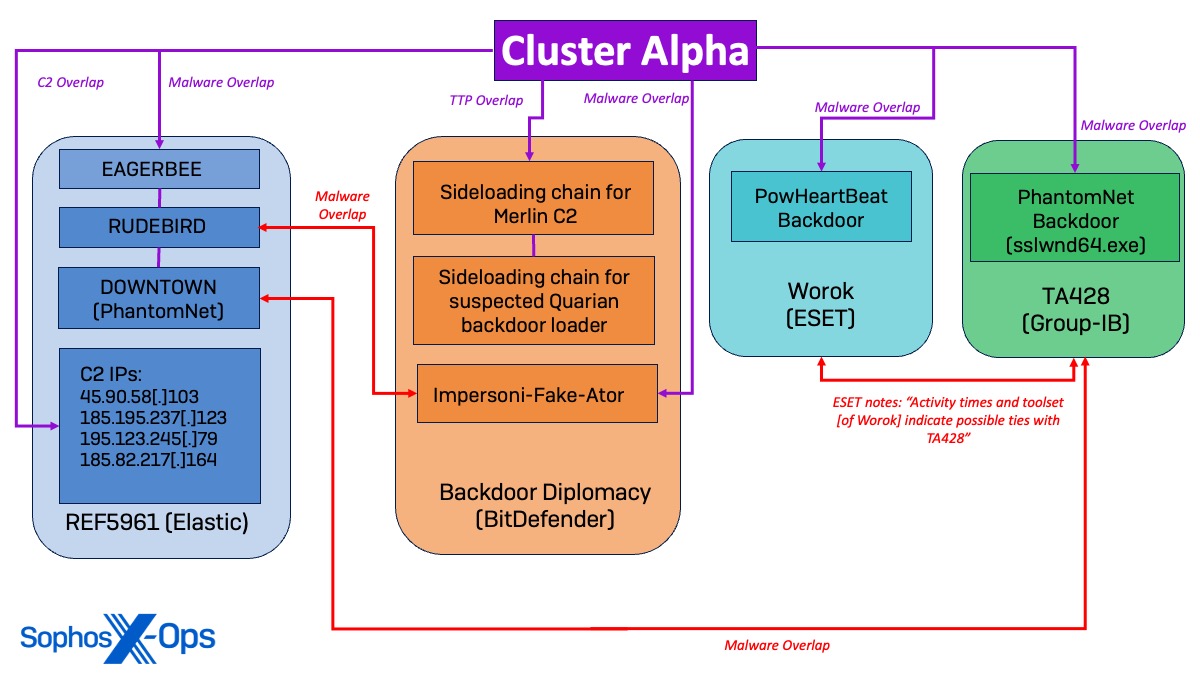
REF5961 Similarities
Three malware variants utilized in Cluster Alpha overlap with malware detailed in an October 2023 report by Elastic Security Labs on a Chinese language-nexus actor tracked as REF5961. Within the article, Elastic particulars REF5961’s use of EAGERBEE, RUDEBIRD, and DOWNTOWN (PhantomNet) malware to focus on the Overseas Affairs Ministry of an Affiliation of Southeast Asian Nations (ASEAN) member. Moreover, malware deployed in Cluster Alpha was noticed connecting to a number of C2 IP addresses linked to REF5961.
BackdoorDiplomacy Similarities
Cluster Alpha exercise additionally aligns with a case research by BitDefender on a cyberespionage marketing campaign within the Center East by a Chinese language menace actor tracked as BackdoorDiplomacy, which is noted to overlap with different reported menace teams resembling APT15, Playful Taurus, Vixen Panda, NICKEL, and Ke3chang.
Sophos MDR hunters noticed the identical sideloading chains described within the BitDefender report back to deploy a Merlin C2 Agent and a suspected loader for the Quarian backdoor. On account of Sophos Endpoint controls, the malicious payload was deleted earlier than execution; nonetheless, the similarity in sideloading procedures suggests a connection between Cluster Alpha and former BackdoorDiplomacy campaigns.
Notably, Sophos Labs documented similarities between the RUDEBIRD malware tracked by Elastic and the Impersoni-Faux-Ator malware detailed by BitDefender, suggesting a possible connection between the REF5961 intrusion set and the Backdoor Diplomacy actor. Whereas it is a noteworthy relation, we acknowledge extra observations and samples are wanted to verify the character of the overlap between these two reported actors with increased confidence.
Worok and TA428 Similarities
As well as, the PowHeartBeat backdoor utilized in Cluster Alpha has been reported by ESET to be attributed to the Worok cyberespionage group, which is famous to have attainable ties to the Chinese language APT TA428. Additional bolstering the connection, the DOWNTOWN (PhantomNet) malware utilized in Cluster Alpha was additionally attributed to TA428 by Elastic, and Sophos noticed the PhantomNet backdoor implant (sslwnd64.exe) shortly after Group-IB Threat Intelligence linked the pattern to suspected TA428 exercise.
Cluster Bravo
The CCoreDoor backdoor utilized in Cluster Bravo exercise bears placing similarity to EtherealGh0st, detailed in a Could 2024 report from BitDefender. EtherealGh0st is related to a Chinese language-nexus actor tracked by BitDefender as Unfading Sea Haze. The malware overlaps with CCoreDoor in its use of the CCore Library and the usage of StartWorkThread to decrypt the C2 hostname and port, in addition to within the instructions the backdoor accepts. There may be additionally area overlap in the usage of the C2 area message.ooguy[.]com—Sophos MDR noticed this C2 speaking with the CCoreDoor backdoor, and BitDefender experiences that the area is referenced within the EtherealGh0st pattern they collected.
Moreover, BitDefender reported the primary use of EtheralGh0st round mid-March 2023, which aligns with our timeline: CCoreDoor was first seen being deployed on March 14, 2023. There may be additionally a similarity in victimology, as Unfading Sea Haze is reported to focus on authorities and army organizations from international locations within the South China Sea.
Cluster Charlie
Earth Longzhi Similarities (APT41)
Although the actor working in Cluster Charlie used a beforehand unreported malware household, their C2 infrastructure overlaps with reporting by Trend Micro on a bunch tracked as Earth Longzhi, which is a reported Chinese language subgroup of APT41.
Sophos noticed the PocoProxy pattern 443.txt speaking with recognized Earth Longzhi C2 IP 198.13.47[.]158 a few month previous to Pattern Micro mentioning that IP deal with of their report. Different infrastructure leveraged in Cluster Charlie aligns with Earth Longzhi’s earlier infrastructure patterns as effectively – particularly the usage of variations on the speedtest[.]com area. On this intrusion, we’ve got noticed the usage of each googlespeedtest33[.]com and <sufferer identify>speedtest[.]com. Equally, two separate Pattern Micro experiences have detailed Earth Longzhi registering speedtest[.]com C2 domains with the same format (vietsovspeedtest[.]com and evnpowerspeedtest[.]com).
Cluster Overlap
Whereas the proof portrays three distinct units of TTPs working at separate instances with customized tooling, there are additionally notable overlaps between them. For instance, there have been some situations of the clusters utilizing the identical credentials, such because the actors in Cluster Alpha and Cluster Bravo utilizing the identical insecure administrator account (which was additionally compromised in an inner penetration take a look at) to carry out actions on completely different methods.
Moreover, whereas the clusters have been energetic on completely different endpoints, they did goal a number of of the identical main servers and area controllers. Nonetheless, they have been not often energetic on the identical server on the identical day, and as detailed beforehand, temporal evaluation of the clusters’ exercise signifies a correlating dynamic within the timing of their operations.
Analyzing the Overlap
In our evaluation of the clusters and the relations between them, we discovered ourselves in a comparable state of affairs to Cybereason’s Nocturnus Staff, who carried out a comparable clustering effort in 2021 targeted on Chinese language focusing on of telecommunication corporations. As talked about, there might be many challenges in figuring out the character of overlaps between clusters, and there are at all times “what ifs?” that play into figuring out what’s going on behind the intrusion exercise in a community.
On this case, the exercise clusters have been noticed in the identical group, throughout the identical timeframe, and even on the identical endpoints. In consequence, figuring out “who did what” could be a difficult job. The evaluation turns into much more advanced when contemplating Chinese language state-sponsored menace teams are generally recognized to share infrastructure and tooling.
Whereas the clusters exhibit distinct patterns of conduct, the delineations within the timing of the clusters’ operations, the overlaps in compromised infrastructure, and similarities of their aims counsel a connection between them. Nonetheless, since we can not decide with excessive confidence what’s going on behind the scenes, we provide two believable hypotheses that would clarify the dynamic between the noticed clusters:
- The noticed clusters replicate the operations of two or extra distinct actors working in tandem with shared aims
- The noticed clusters replicate the work of a single group with a big array of instruments, various infrastructure, and a number of operators
At present, most of our proof factors to the primary speculation being the almost definitely primarily based on the extent of coordination we’ve got noticed; nonetheless, we acknowledge extra info is required to verify that evaluation with increased confidence. These might evolve as our intelligence assortment continues and new proof emerges which will present additional perception into the identities and relations of the noticed clusters.
Conclusions
Based mostly on our evaluation, we assess with average confidence that a number of distinct Chinese language state-sponsored actors have been energetic on this high-profile Southeast Asian authorities group since no less than March 2022. Although we’re at the moment unable to carry out high-confidence attribution or affirm the character of the connection between these clusters, our present investigation means that the clusters replicate the work of separate actors tasked by a government with parallel aims in pursuit of Chinese language state pursuits.
Whereas this report is concentrated on Crimson Palace exercise by August of 2023, we proceed to watch associated intrusion exercise focusing on this group. Following our actions to dam the actors’ C2 implants in August, the menace actors went quiet for a a number of week interval. Cluster Alpha’s final energetic recognized implant ceased C2 communications in August 2023, and we’ve got not seen the cluster of exercise re-emerge within the sufferer community. Nonetheless, the identical can’t be stated for Cluster Charlie.
After just a few weeks of dormancy, we noticed the actors in Cluster Charlie re-penetrate the community by way of an internet shell and resume their exercise at the next tempo and in a extra evasive method. They started performing actions on aims throughout the community, together with exfiltration efforts in November. Moreover, as an alternative of leaving their implants on disks for lengthy durations of time, the actors used completely different situations of their net shell to re-penetrate the community for his or her classes and commenced to modulate completely different C2 channels and strategies of deploying implants on course methods.
Sophos MDR menace hunters proceed to observe and examine intrusion exercise on this community, and we proceed to share intelligence with the group.
This cyberespionage marketing campaign was uncovered by Sophos MDR’s human-led menace looking service, which performs a crucial position in proactively figuring out menace exercise. Along with augmenting MDR operations, the MDR menace looking service feeds into our SophosLabs pipeline to supply enriched safety and detections.
The investigation into the marketing campaign demonstrates the significance of an environment friendly intelligence cycle, outlining how a menace hunt spawned from a raised detection can generate intelligence to develop new detections and jumpstart extra hunts.
Indicators of Compromise
The next linked information on Sophos’ GitHub web page include IoCs for every of the units of exercise described on this report. Moreover, we’ve got supplied IoCs from exercise after August of 2023 associated to this case:
Acknowledgements:
Sophos X-Ops acknowledges the contributions of Colin Cowie, Jordon Olness, Hunter Neal, Andrew Jaeger, Pavle Culum, Kostas Tsialemis, and Daniel Souter of Sophos Managed Detection and Response, and Gabor Szappanos, Andrew Ludgate, and Steeve Gaudreault of SophosLabs to this report.









