
Menace actors impersonate GitHub’s safety and recruitment groups in phishing assaults to hijack repositories utilizing malicious OAuth apps in an ongoing extortion marketing campaign wiping compromised repos.
Since not less than February, dozens of developers focused on this marketing campaign have acquired comparable pretend job offers or security alert emails from “notifications@github.com” after being tagged in spam feedback added to random repo points or pull requests utilizing compromised GitHub accounts.
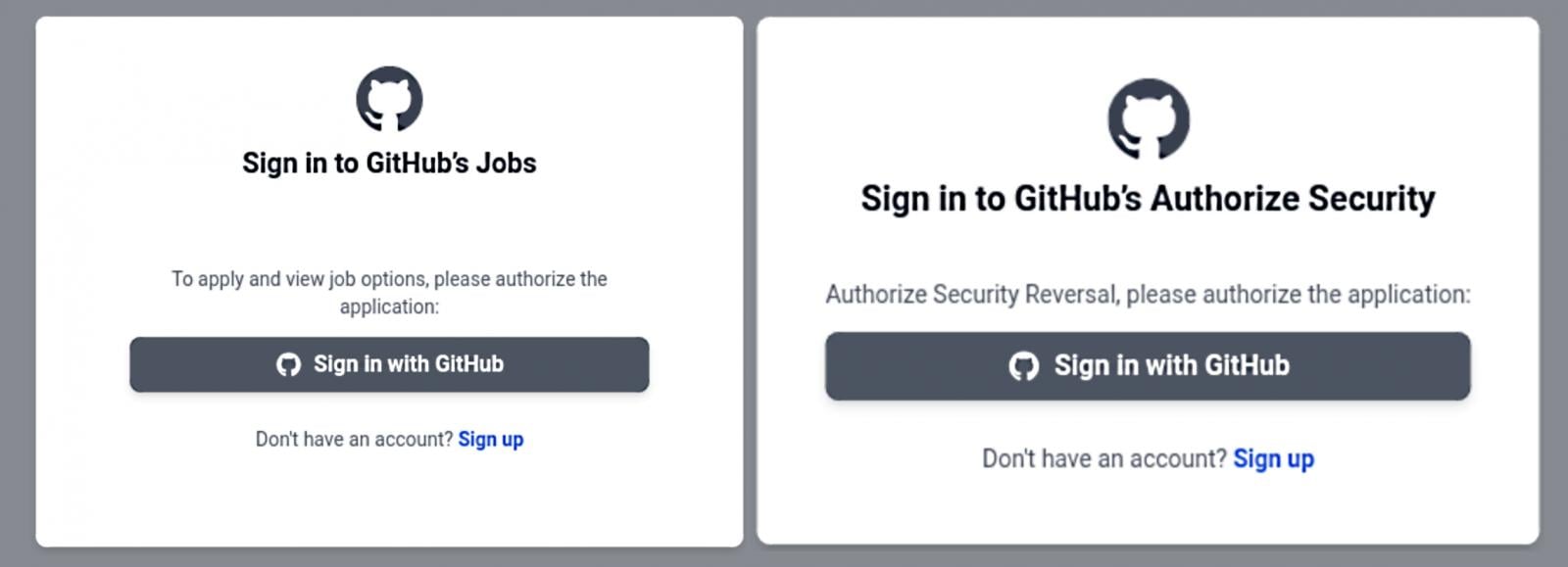
The phishing emails redirect potential victims to githubcareers[.]on-line or githubtalentcommunity[.]on-line, as first spotted by CronUp safety researcher Germán Fernández.
On the touchdown pages, customers are requested to signal into their GitHub accounts to authorize a brand new OAuth app that requests entry to non-public repositories, private consumer knowledge, and the flexibility to delete any adminable repository, amongst different issues.
Many GitHub customers who’ve fallen sufferer to those assaults additionally report having their accounts disabled and shedding entry to all repos—probably after different victims reported them for being abused to push remark spam.
As BleepingComputer reported on Thursday, after having access to the victims’ repositories, the attackers wipe the contents, rename the repository, and add a README.me file instructing the victims to succeed in out on Telegram to get better the info.
In addition they declare to have stolen the victims’ knowledge earlier than destroying it and created a backup that might assist restore the wiped repositories.
BleepingComputer has but to obtain a reply from a GitHub spokesperson after reaching out final week for extra particulars concerning the Gitloker extortion marketing campaign.
Nevertheless, GitHub employees has been replying to neighborhood discussions about these assaults since February, saying the marketing campaign targets GitHub’s point out and notification performance and asking these focused to report this malicious exercise utilizing the coding platform’s abuse reporting tools.
“We perceive the inconvenience attributable to these notifications. Our groups are presently engaged on addressing these unsolicited phishing notifications,” one GitHub neighborhood supervisor said.
“We wish to remind our customers to proceed to make use of our abuse reporting instruments to boost any abusive or suspicious exercise. This can be a phishing marketing campaign and isn’t the results of a compromise of GitHub or its techniques.”
GitHub employees additionally suggested customers to take the next measures to make sure their accounts aren’t hijacked in these assaults:
In September 2020, GitHub warned of one other phishing marketing campaign utilizing emails pushing pretend CircleCI notifications to steal GitHub credentials and two-factor authentication (2FA) codes by relaying them by way of reverse proxies.








